At ValidExamDumps, we consistently monitor updates to the Oracle 1Z0-116 exam questions by Oracle. Whenever our team identifies changes in the exam questions,exam objectives, exam focus areas or in exam requirements, We immediately update our exam questions for both PDF and online practice exams. This commitment ensures our customers always have access to the most current and accurate questions. By preparing with these actual questions, our customers can successfully pass the Oracle Database Security Administration exam on their first attempt without needing additional materials or study guides.
Other certification materials providers often include outdated or removed questions by Oracle in their Oracle 1Z0-116 exam. These outdated questions lead to customers failing their Oracle Database Security Administration exam. In contrast, we ensure our questions bank includes only precise and up-to-date questions, guaranteeing their presence in your actual exam. Our main priority is your success in the Oracle 1Z0-116 exam, not profiting from selling obsolete exam questions in PDF or Online Practice Test.
Database Vault is configured and enabled in the database. You create a rule set to enforce security on the hr. employees table.
Examine these requirements:
1. Users working In hr department are allowed to view all rows In HR.EMPLOYEES.
2. hr managers are allowed to view, update, and delete data in In HR.EMPLOYEES.
3. Audit records are to be collected for every evaluation of the rule set.
Which two options are true when creating the rule set?
A DBA user created and configured this secure application role:
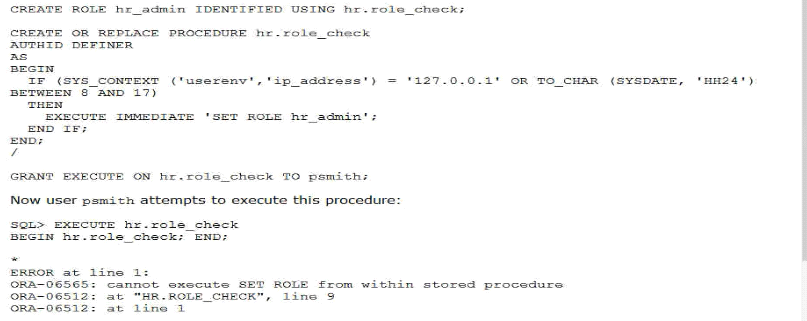
Why does the error occur?
Which two statements are true about the Secure External Password Store (SEPS)?