At ValidExamDumps, we consistently monitor updates to the Netskope NSK101 exam questions by Netskope. Whenever our team identifies changes in the exam questions,exam objectives, exam focus areas or in exam requirements, We immediately update our exam questions for both PDF and online practice exams. This commitment ensures our customers always have access to the most current and accurate questions. By preparing with these actual questions, our customers can successfully pass the Netskope Certified Cloud Security Administrator Exam exam on their first attempt without needing additional materials or study guides.
Other certification materials providers often include outdated or removed questions by Netskope in their Netskope NSK101 exam. These outdated questions lead to customers failing their Netskope Certified Cloud Security Administrator Exam exam. In contrast, we ensure our questions bank includes only precise and up-to-date questions, guaranteeing their presence in your actual exam. Our main priority is your success in the Netskope NSK101 exam, not profiting from selling obsolete exam questions in PDF or Online Practice Test.
Your company started deploying the latest version of the Netskope Client and you want to track the progress and device count using Netskope.
Which two statements are correct in this scenario? (Choose two.)
To track the progress and device count of the latest Netskope Client deployment, you can use the following methods:
Use Netskope Digital Experience Management to monitor the status:
Netskope Digital Experience Management (DEM) provides visibility into the performance and status of applications and devices. You can use this tool to monitor the deployment status and ensure that the new client version is being deployed correctly across the organization.
Use the Devices page under Settings to view and filter the required data:
The Devices page in the Netskope console provides detailed information about all devices managed by Netskope. You can filter this data to view the specific deployment status of the latest Netskope Client version, helping you track the progress and identify any issues.
Netskope Knowledge Portal: Digital Experience Management
Netskope Knowledge Portal: Devices Page
What are two primary advantages of Netskope's Secure Access Service Edge (SASE) architecture? (Choose two.
What information is displayed in an application's Cloud Confidence Index (CCI) page? (Choose two.)
The Cloud Confidence Index (CCI) page in Netskope provides various metrics and information about an application. Among these, the two relevant pieces of information displayed are:
Top users by sessions: This metric provides insights into which users are most active within the application, giving a view of user engagement and activity levels.
GDPR readiness: This metric indicates how well the application complies with GDPR regulations, providing a readiness score or status based on the app's handling of personal data.
These metrics help administrators and security professionals to evaluate the usage and compliance status of cloud applications.
Click the Exhibit button.
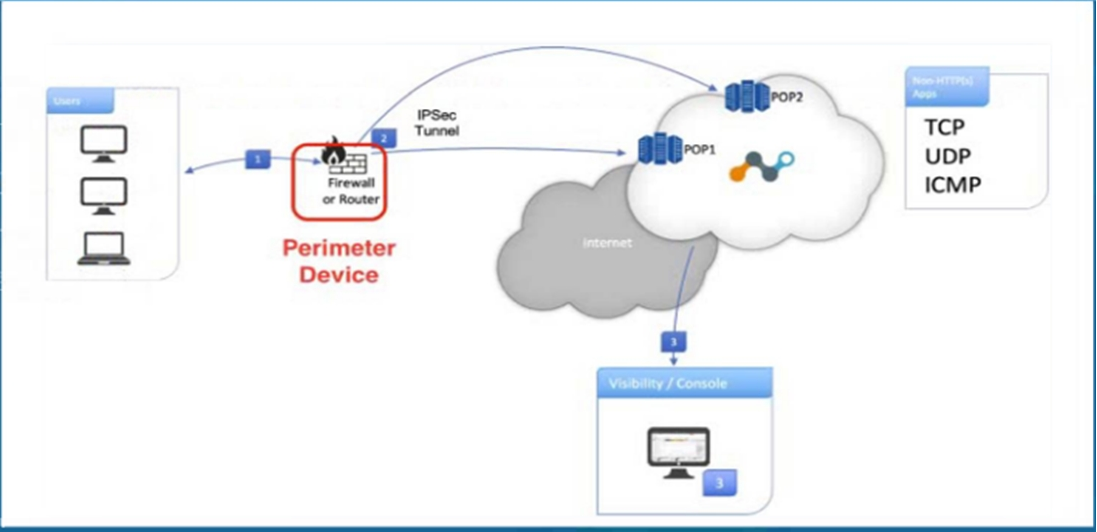
Referring to the exhibit, what are two recommended steps to be set on the perimeter device to monitor IPsec tunnels to a Netskope data plane? (Choose two.)
To monitor IPsec tunnels to a Netskope data plane, it is essential to ensure the stability and responsiveness of the tunnels. The recommended steps involve enabling monitoring mechanisms that detect and respond to tunnel failures. Here's a detailed explanation of the two recommended steps:
Enable IKE Dead Peer Detection (DPD) for each tunnel:
Implementation: Configure DPD in the IPsec settings of the perimeter device. This ensures that if the Netskope data plane is unreachable, the tunnel is automatically terminated and re-negotiated.
Send ICMP requests to the Netskope location's Probe IP:
Implementation: Set up regular ICMP requests (ping) from the perimeter device to the Netskope Probe IPs. This allows for continuous monitoring of the tunnel's health and immediate detection of connectivity issues.
REST API v2 Overview - Netskope Knowledge Portal
Using the REST API v2 dataexport Iterator Endpoints - Netskope Knowledge Portal
Using the REST API v2 UCI Impact Endpoints - Netskope Knowledge Portal