At ValidExamDumps, we consistently monitor updates to the Microsoft MS-500 exam questions by Microsoft. Whenever our team identifies changes in the exam questions,exam objectives, exam focus areas or in exam requirements, We immediately update our exam questions for both PDF and online practice exams. This commitment ensures our customers always have access to the most current and accurate questions. By preparing with these actual questions, our customers can successfully pass the Microsoft 365 Security Administration exam on their first attempt without needing additional materials or study guides.
Other certification materials providers often include outdated or removed questions by Microsoft in their Microsoft MS-500 exam. These outdated questions lead to customers failing their Microsoft 365 Security Administration exam. In contrast, we ensure our questions bank includes only precise and up-to-date questions, guaranteeing their presence in your actual exam. Our main priority is your success in the Microsoft MS-500 exam, not profiting from selling obsolete exam questions in PDF or Online Practice Test.
You have a Microsoft 365 E5 subscription that contains 1,000 Windows 10 devices. The devices are onboarded to Microsoft Defender for Endpoint.
You need to view a consolidated list of the common vulnerabilities and exposures (CVE) that affect the devices. The solution must minimize administrative effort.
Which Threat & Vulnerability Management page should you use?
You need to create Group3.
What are two possible ways to create the group?
You have a Microsoft 165 ES subscription that contains users named User 1 and User2?
You have the audit log retention requirements shown in the following table.
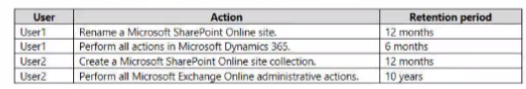
You need to create audit retention policies to meet the requirements. The solution must minimize cost and the number of policies.
What is the minimum number of audit retention policies that you should create?
You have a Microsoft 365 subscription.
You have a team named Team1 in Microsoft Teams.
You plan to place all the content in Team1 on hold.
You need to identify which mailbox and which Microsoft SharePoint site collection are associated to Team1.
Which cmdlet should you use?