At ValidExamDumps, we consistently monitor updates to the Microsoft MS-100 exam questions by Microsoft. Whenever our team identifies changes in the exam questions,exam objectives, exam focus areas or in exam requirements, We immediately update our exam questions for both PDF and online practice exams. This commitment ensures our customers always have access to the most current and accurate questions. By preparing with these actual questions, our customers can successfully pass the Microsoft 365 Identity and Services exam on their first attempt without needing additional materials or study guides.
Other certification materials providers often include outdated or removed questions by Microsoft in their Microsoft MS-100 exam. These outdated questions lead to customers failing their Microsoft 365 Identity and Services exam. In contrast, we ensure our questions bank includes only precise and up-to-date questions, guaranteeing their presence in your actual exam. Our main priority is your success in the Microsoft MS-100 exam, not profiting from selling obsolete exam questions in PDF or Online Practice Test.
You have a Microsoft 365 F5 subscription and the Windows 11 devices shown in the following table.
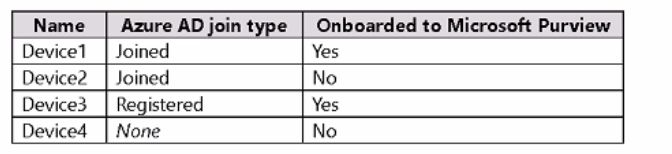
All the devices have Microsoft 365 Apps for enterprise installed.
From the Microsoft 365 Apps admin renter, you create a policy configuration named Policy1 and apply Policy1 to all users.
On which devices is Policy1 applied?
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these
questions will not appear in the review screen.
You have a Microsoft 365 subscription.
You discover that some external users accessed content on a Microsoft SharePoint site. You modify the
SharePoint sharing policy to prevent sharing outside your organization.
You need to be notified if the SharePoint policy is modified in the future.
Solution: From the Security & Compliance admin center, you create a threat management policy.
Does this meet the goal?
We can create a threat management policy to alert us when the sharing policy is changed.
Create a new Alert policy > under Category select Threat Management > under 'Activity is' scroll down to the 'Site administration activities' and select 'Changed a sharing policy'.
You have a Microsoft 365 subscription that contains the domains shown in the following exhibit.
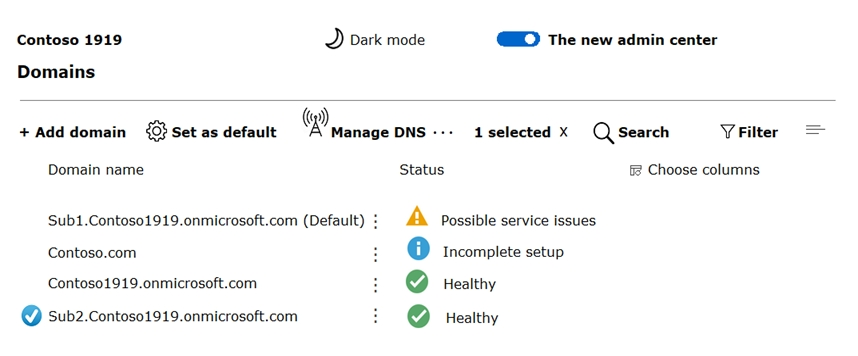
Which domain name suffixes can you use when you create users?
Your company has a Microsoft 365 subscription.
You upload several archive PST files to Microsoft 365 by using the Security & Compliance admin center.
A month later, you attempt to run an import job for the PST files.
You discover that the PST files were deleted from Microsoft 365.
What is the most likely cause of the files being deleted? More than one answer choice may achieve the goal.
Select the BEST answer.
https://docs.microsoft.com/en-us/office365/securitycompliance/faqimporting-pst-files-to-office-365
You can use the Office 365 Import Service to bulk-import PST files to Office 365 mailboxes.
When you use the network upload method to import PST files, you upload them to an Azure blob container named ingestiondata. If there are no import jobs in progress on the Import page in the Security & Compliance Center), then all PST files in the ingestiondata container in Azure are deleted 30 days after the most recent import job was created in the Security & Compliance Center.
https://docs.microsoft.com/en-us/office365/securitycompliance/faqimporting-pst-files-to-office-365
You need to meet the security requirement for the vendors.
What should you do?
You can invite guest users to the directory, to a group, or to an application. After you invite a user through any of these methods, the invited user's account is added to Azure Active Directory (Azure AD), with a user type of Guest. The guest user must then redeem their invitation to access resources. An invitation of a user does not expire.
The invitation will include a link to create a Microsoft account. The user can then authenticate using their Microsoft account. In this question, the vendors already have Microsoft accounts so they can authenticate using them.
https://docs.microsoft.com/en-us/azure/active-directory/b2b/add-users-administrator