At ValidExamDumps, we consistently monitor updates to the Microsoft MD-100 exam questions by Microsoft. Whenever our team identifies changes in the exam questions,exam objectives, exam focus areas or in exam requirements, We immediately update our exam questions for both PDF and online practice exams. This commitment ensures our customers always have access to the most current and accurate questions. By preparing with these actual questions, our customers can successfully pass the Microsoft Windows Client exam on their first attempt without needing additional materials or study guides.
Other certification materials providers often include outdated or removed questions by Microsoft in their Microsoft MD-100 exam. These outdated questions lead to customers failing their Microsoft Windows Client exam. In contrast, we ensure our questions bank includes only precise and up-to-date questions, guaranteeing their presence in your actual exam. Our main priority is your success in the Microsoft MD-100 exam, not profiting from selling obsolete exam questions in PDF or Online Practice Test.
You have 100 computers that run Windows 10. The computers are in a workgroup.
The computers have a low-bandwidth metered Internet connection.
You need to reduce the amount of Internet bandwidth consumed to download updates.
What should you configure?
You have an Azure Active Directory (Azure AD) tenant named contoso.com.
You have a workgroup computer named Computer1 that runs Windows 10.
You need to add Computer1 to contoso.com.
What should you use?
You join a computer to a domain, including an Azure AD domain in the Settings panel in Windows 10, under System->About
Your network contains an Active Directory domain. The domain contains two computers named Computer1 and Computer2 that run Windows 10.
You need to modify the registry of Computer1 by using Registry Editor from Computer2.
Which two registry hives can you modify? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
Your network contains an Active Directory domain. The domain contains a computer named Computer1 that runs Windows 10. Computer1 contains a folder named Folder1.
You plan to share Folder1. Everyone will have Read share permissions, and administrators will have Full control share permission.
You need to prevent the share from appearing when users browse the network.
What should you do?
Appending a dollar sign to share name prevents a share from appearing when users browse the network.
Incorrect Answers:
Access-based enumeration will hide the share from anyone who doesn't have permission to access the share. However, as 'Everyone' has Read access to the share, the share would appear for everyone when they browse the network.
You have a computer that is configured as shown in the following exhibit.
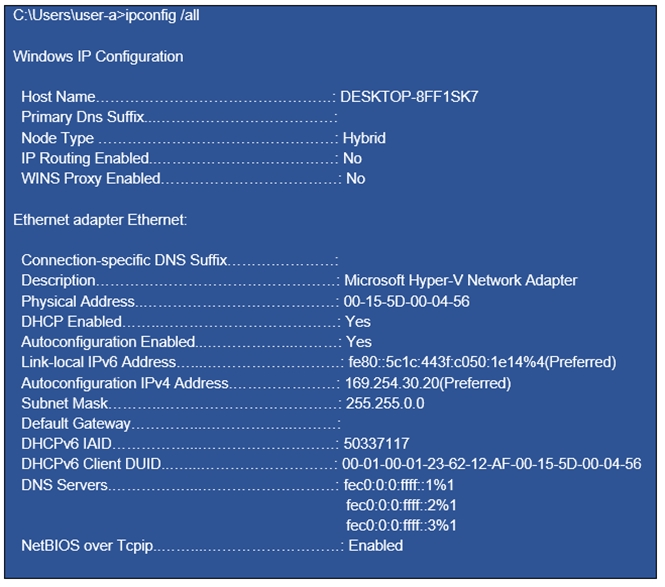
What can the computer connect to?