At ValidExamDumps, we consistently monitor updates to the Microsoft AZ-220 exam questions by Microsoft. Whenever our team identifies changes in the exam questions,exam objectives, exam focus areas or in exam requirements, We immediately update our exam questions for both PDF and online practice exams. This commitment ensures our customers always have access to the most current and accurate questions. By preparing with these actual questions, our customers can successfully pass the Microsoft Azure IoT Developer exam on their first attempt without needing additional materials or study guides.
Other certification materials providers often include outdated or removed questions by Microsoft in their Microsoft AZ-220 exam. These outdated questions lead to customers failing their Microsoft Azure IoT Developer exam. In contrast, we ensure our questions bank includes only precise and up-to-date questions, guaranteeing their presence in your actual exam. Our main priority is your success in the Microsoft AZ-220 exam, not profiting from selling obsolete exam questions in PDF or Online Practice Test.
You use Azure Security Center in an Azure IoT solution.
You need to exclude some security events. The solution must minimize development effort. What should you do?
Properties related to every Azure Security Center for IoT security agent are located in the agent configuration object, within the desired properties section, of the azureiotsecurity module.
To modify the configuration, create and modify this object inside the azureiotsecurity module twin identity. Note: Azure Security Center for IoT's security agent twin configuration object is a JSON format object. The
configuration object is a set of controllable properties that you can define to control the behavior of the agent.
These configurations help you customize the agent for each scenario required. For example, automatically excluding some events, or keeping power consumption to a minimal level are possible by configuring these properties.
https://docs.microsoft.com/en-us/azure/asc-for-iot/how-to-agent-configuration
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Standard tier Azure IoT hub and a fleet of IoT devices.
The devices connect to the IoT hub by using either Message Queuing Telemetry Transport (MQTT) or Advanced Message Queuing Protocol (AMQP).
You need to send data to the IoT devices and each device must respond. Each device will require three minutes to process the data and respond.
Solution: You use cloud-to-device messages and watch the cloud-to-device feedback endpoint for successful acknowledgement.
Does this meet the goal?
IoT Hub provides three options for device apps to expose functionality to a back-end app:
Twin's desired properties for long-running commands intended to put the device into a certain desired state. For example, set the telemetry send interval to 30 minutes.
Direct methods for communications that require immediate confirmation of the result. Direct methods are often used for interactive control of devices such as turning on a fan.
Cloud-to-device messages for one-way notifications to the device app.
https://docs.microsoft.com/en-us/azure/iot-hub/iot-hub-devguide-c2d-guidance
You have 10 devices that connect to an Azure loT hub. Each device has a unique public IP address. The devices are not provisioned through DPS.
You discover an anomaly in messages from two devices.
You need to stop all messages from both devices without affecting the other devices.
Solution: You add IP filter rules for the devices.
Does this meet the goal?
You have an Azure IoT hub that uses a Device Provisioning Service instance.
You have 1,000 legacy IoT devices that only support MAC address or serial number identities. The device do NOT have a security feature that can be used to securely identify the device or a hardware security module (HSM).
You plan to deploy the devices to a secure environment.
You need to configure the Device Provisioning Service instance to ensure that all the devices are identified securely before they receive updates.
Which attestation mechanism should you choose?
A common problem with many legacy devices is that they often have an identity that is composed of a single piece of information. This identity information is usually a MAC address or a serial number. Legacy devices may not have a certificate, TPM, or any other security feature that can be used to securely identify the device. The Device Provisioning Service for IoT hub includes symmetric key attestation. Symmetric key attestation can be used to identify a device based off information like the MAC address or a serial number.
https://docs.microsoft.com/bs-latn-ba/azure/iot-dps/how-to-legacy-device-symm-key
You have an Azure subscription that contains the resources shown in the following table.
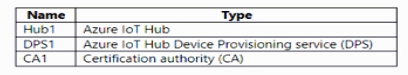
You create a group enrollment in DPS1 and enroll 100 loT devices. Each device is issued a leaf certificate from CAT. You need to deprovision a single loT device from the group enrollment. The solution must not affect the other devices. Solution: You delete the device entry from the device registry of Hub1. Does this meet the goal?