At ValidExamDumps, we consistently monitor updates to the Juniper JN0-637 exam questions by Juniper. Whenever our team identifies changes in the exam questions,exam objectives, exam focus areas or in exam requirements, We immediately update our exam questions for both PDF and online practice exams. This commitment ensures our customers always have access to the most current and accurate questions. By preparing with these actual questions, our customers can successfully pass the Juniper Security, Professional exam on their first attempt without needing additional materials or study guides.
Other certification materials providers often include outdated or removed questions by Juniper in their Juniper JN0-637 exam. These outdated questions lead to customers failing their Juniper Security, Professional exam. In contrast, we ensure our questions bank includes only precise and up-to-date questions, guaranteeing their presence in your actual exam. Our main priority is your success in the Juniper JN0-637 exam, not profiting from selling obsolete exam questions in PDF or Online Practice Test.
You are asked to create multiple virtual routers using a single SRX Series device. You must ensure that each virtual router maintains a unique copy of the routing protocol daemon (RPD) process.
Which solution will accomplish this task?
Logical systems on SRX Series devices allow the creation of separate virtual routers, each with its unique RPD process. This segmentation ensures that routing and security policies are isolated across different logical systems, effectively acting like independent routers within a single SRX device. For further information, see Juniper Logical Systems Documentation.
To create multiple virtual routers on a single SRX Series device, each with its own unique copy of the routing protocol daemon (RPD) process, you need to use logical systems. Logical systems allow for the segmentation of an SRX device into multiple virtual routers, each with independent configurations, including routing instances, policies, and protocol daemons.
Explanation of Answer D (Logical System):
A logical system on an SRX device enables you to create multiple virtual instances of the SRX, each operating independently with its own control plane and routing processes. Each logical system gets a separate copy of the RPD process, ensuring complete isolation between virtual routers.
This is the correct solution when you need separate routing instances with their own RPD processes on the same physical device.
Configuration Example:
bash
set logical-systems <logical-system-name> interfaces ge-0/0/0 unit 0
set logical-systems <logical-system-name> routing-options static route 0.0.0.0/0 next-hop 192.168.1.1
Juniper Security Reference:
Logical Systems Overview: Logical systems allow for the creation of multiple virtual instances within a single SRX device, each with its own configuration and control plane. Reference: Juniper Logical Systems Documentation.
A user reports that a specific application is not working properly. This application makes
multiple connection to the server and must have the same address every time from a pool and this behavior needs to be changed.
What would solve this problem?
Referring to the exhibit,
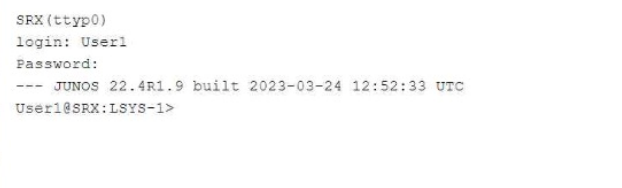
which two statements about User1 are true? (Choose two.)
In this configuration, User1 is logged into logical system LSYS-1, which restricts access and visibility to that particular system. This ensures isolation between logical systems on the same physical device. Only a system administrator can assign additional permissions. For more details, see Juniper Logical Systems Guide.
From the exhibit, we see that User1 is logged into logical system LSYS-1:
Access to Assigned Logical System (Answer A): User1, being logged into the logical system LSYS-1, only has access to the configuration and interfaces within that logical system. This is a key feature of logical systems in Junos, ensuring users are restricted to their respective environments.
Logged into LSYS-1 (Answer B): The prompt shows that User1 is currently operating in LSYS-1, as indicated by the User1@SRX:LSYS-1> command line.
You are using AutoVPN to deploy a hub-and-spoke VPN to connect your enterprise sites.
In this scenario, which two statements are true? (Choose two.)
You want to enable transparent mode on your SRX series device.
In this scenario, which three actions should you perform? (Choose three.)