At ValidExamDumps, we consistently monitor updates to the Juniper JN0-1332 exam questions by Juniper. Whenever our team identifies changes in the exam questions,exam objectives, exam focus areas or in exam requirements, We immediately update our exam questions for both PDF and online practice exams. This commitment ensures our customers always have access to the most current and accurate questions. By preparing with these actual questions, our customers can successfully pass the Juniper Security Design, Specialist Exam exam on their first attempt without needing additional materials or study guides.
Other certification materials providers often include outdated or removed questions by Juniper in their Juniper JN0-1332 exam. These outdated questions lead to customers failing their Juniper Security Design, Specialist Exam exam. In contrast, we ensure our questions bank includes only precise and up-to-date questions, guaranteeing their presence in your actual exam. Our main priority is your success in the Juniper JN0-1332 exam, not profiting from selling obsolete exam questions in PDF or Online Practice Test.
When two security services process a packet whether it is being processed in the first-packet path or the fast path? (Choose two.)
You must design a separate network within your trust network with added security and separation. What is the common name for this type of network?
Refer to the exhibit.
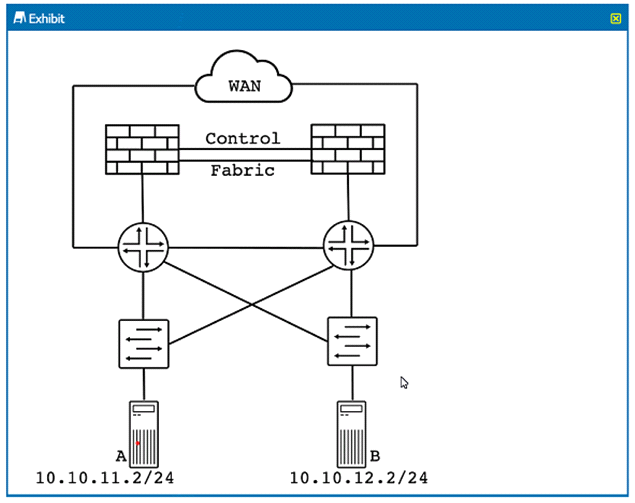
The SRX Series devices are decoyed in an off-path active/passive Cluster configuration
What are two advantages of this deployment model over an active-'active duster configuration' (Choose two)
You must ensure that all 10GbE interfaces have an MTU of 9192 and that an of the ge-0/0>4.0 interfaces on the SRX Series devices are in a specific zone.
Which type of a script would you use to accomplish this task?