At ValidExamDumps, we consistently monitor updates to the Fortinet NSE7_ADA-6.3 exam questions by Fortinet. Whenever our team identifies changes in the exam questions,exam objectives, exam focus areas or in exam requirements, We immediately update our exam questions for both PDF and online practice exams. This commitment ensures our customers always have access to the most current and accurate questions. By preparing with these actual questions, our customers can successfully pass the Fortinet NSE 7 - Advanced Analytics 6.3 exam on their first attempt without needing additional materials or study guides.
Other certification materials providers often include outdated or removed questions by Fortinet in their Fortinet NSE7_ADA-6.3 exam. These outdated questions lead to customers failing their Fortinet NSE 7 - Advanced Analytics 6.3 exam. In contrast, we ensure our questions bank includes only precise and up-to-date questions, guaranteeing their presence in your actual exam. Our main priority is your success in the Fortinet NSE7_ADA-6.3 exam, not profiting from selling obsolete exam questions in PDF or Online Practice Test.
Refer to the exhibit.
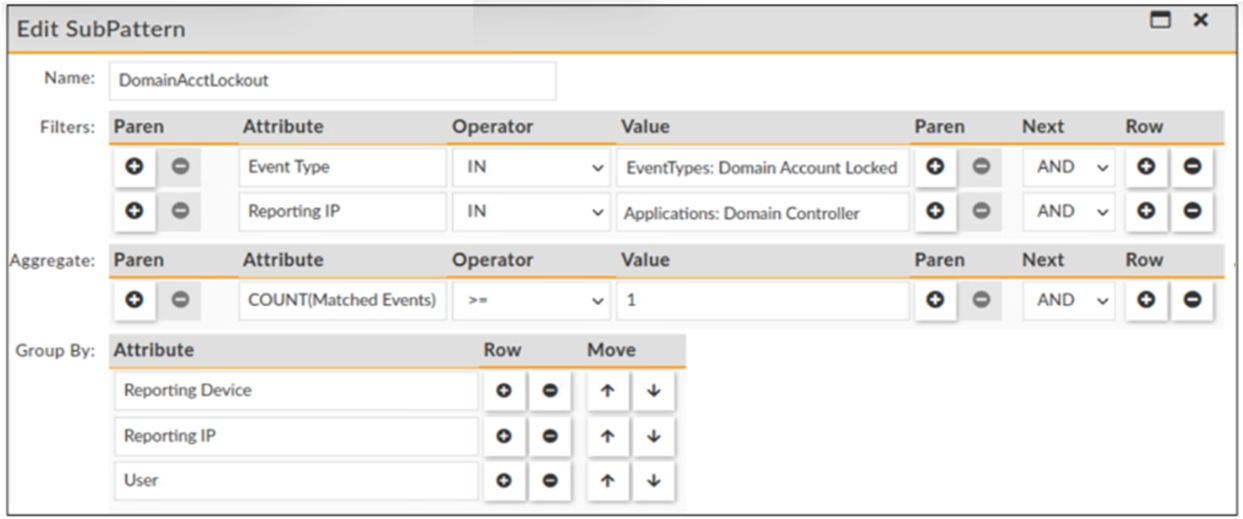
Which statement about the rule filters events shown in the exhibit is true?
The rule filters events with an event type that belong to the Domain Account Locked CMDB group and a reporting IP that belong to the Domain Controller applications group. This means that only events that have both criteria met will be processed by this rule. The event type and reporting IP are joined by an AND operator, which requires both conditions to be true.
Why can collectors not be defined before the worker upload address is set on the supervisor?
Collectors cannot be defined before the worker upload address is set on the supervisor because collectors receive the worker upload address during the registration process. The worker upload address is a list of IP addresses of worker nodes that can receive event data from collectors. The supervisor provides this list to collectors when they register with it, so that collectors can upload event data to any node in the list.
What is Tactic in the MITRE ATT&CK framework?
Tactic is what an attacker hopes to achieve in the MITRE ATT&CK framework. Tactic is a high-level category of adversary behavior that describes their objective or goal. For example, some tactics are Initial Access, Persistence, Lateral Movement, Exfiltration, etc. Each tactic consists of one or more techniques that describe how an attacker can accomplish that tactic.
Refer to the exhibit.
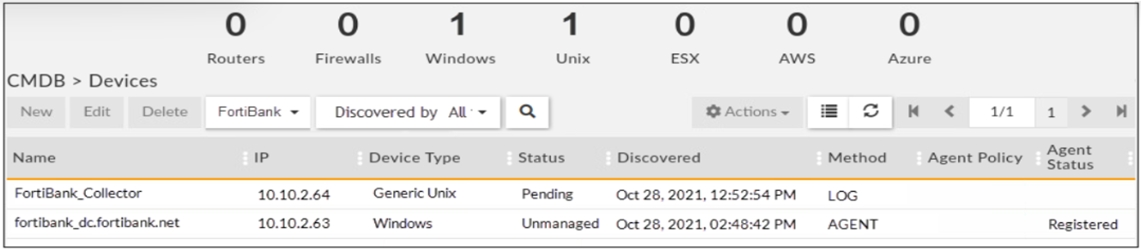
Is the Windows agent delivering event logs correctly?
The windows agent is not delivering event logs correctly because the agent is unmanaged, meaning it is not assigned to any organization or customer. The supervisor will drop the logs silently from unmanaged agents, as they are not associated with any valid license or CMDB.