At ValidExamDumps, we consistently monitor updates to the Fortinet NSE6_FSW-7.2 exam questions by Fortinet. Whenever our team identifies changes in the exam questions,exam objectives, exam focus areas or in exam requirements, We immediately update our exam questions for both PDF and online practice exams. This commitment ensures our customers always have access to the most current and accurate questions. By preparing with these actual questions, our customers can successfully pass the Fortinet NSE 6 - FortiSwitch 7.2 exam on their first attempt without needing additional materials or study guides.
Other certification materials providers often include outdated or removed questions by Fortinet in their Fortinet NSE6_FSW-7.2 exam. These outdated questions lead to customers failing their Fortinet NSE 6 - FortiSwitch 7.2 exam. In contrast, we ensure our questions bank includes only precise and up-to-date questions, guaranteeing their presence in your actual exam. Our main priority is your success in the Fortinet NSE6_FSW-7.2 exam, not profiting from selling obsolete exam questions in PDF or Online Practice Test.
An administrator needs to deploy managed FortiSwitch devices in a remote location where multiple VLANs must be utilized to segment devices. No Layer 3 switch or router is present. The the only WAN connectivity is the router provided by the ISP connected to the public internet.
Which two items will the administrator need to use? (Choose two.)
To deploy FortiSwitch in a remote location with multiple VLANs and no Layer 3 switch or router, you would need specific configurations:
VXLAN Interfaces (B):
Purpose: VXLAN (Virtual Extensible LAN) allows network segmentation without a Layer 3 device, extending VLAN capabilities across dispersed geographical locations over the WAN.
Implementation: Configuring VXLAN on both FortiSwitch and FortiGate can encapsulate Layer 2 traffic over a Layer 3 network, making it ideal for scenarios lacking dedicated routing hardware.
Appropriate Hardware (D):
Requirement: Not all FortiSwitch models might support advanced features like VXLAN; hence, ensuring that the hardware can support such configurations is crucial.
Which two statements about managing a FortiSwitch stack on FortiGate are true? (Choose two.)
A FortiLink interface must be enabled on FortiGate (A): To manage a FortiSwitch stack, a dedicated FortiLink interface on the FortiGate is required. This interface is used to manage the communication between FortiGate and the FortiSwitch stack, enabling centralized control and configuration of the switches directly from the FortiGate.
The switch controller feature must be enabled on FortiGate (B): Enabling the switch controller feature on FortiGate allows it to manage connected FortiSwitch units. This feature provides tools and interfaces on the FortiGate for overseeing FortiSwitch configurations, monitoring switch status, and managing network policies across the stack.
Which statement about the configuration of VLANs on a managed FortiSwitch port is true?
The native VLAN is implicitly part of the allowed VLAN on the port (C): On a managed FortiSwitch port, the native VLAN, which is the VLAN assigned to untagged traffic, is implicitly included in the list of allowed VLANs. This means it does not need to be explicitly specified when configuring VLAN settings on the port. This configuration simplifies VLAN management and ensures that untagged traffic is handled correctly without additional configuration steps.
Refer to the exhibit.
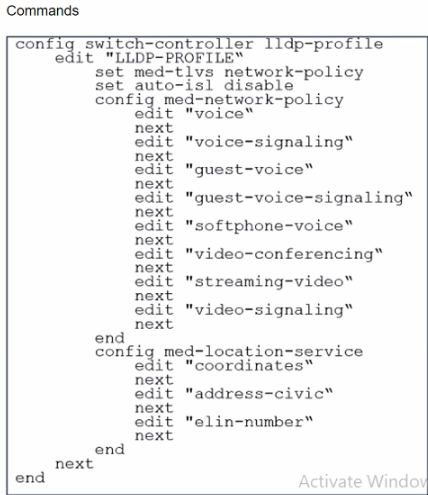
The profile shown in the exhibit is assigned to a group of managed FortiSwitch ports, and these ports are connected to endpoints which are powered by PoE.
Which configuration action can you perform on the LLDP profile to cause these endpoints to exchange PoE information and negotiate power with the managed FortiSwitch?
To cause endpoints to exchange PoE information and negotiate power with the managed FortiSwitch via LLDP, you should configure the LLDP profile to include power management in the advertised LLDP-MED TLVs. Here are the steps:
Access the LLDP Profile Configuration: Start by entering the LLDP profile configuration mode with the command:
config switch-controller lldp-profile
edit 'LLDP-PROFILE'
Enable MED-TLVs: Ensure that MED-TLVs (Media Endpoint Discovery TLVs) are enabled. These TLVs are used for extended discovery relating to network policies, including PoE, and are essential for PoE negotiation. They include power management which is crucial for the negotiation of PoE parameters between devices. The command to ensure network policies are set might look like:
set med-tlvs network-policy
Add Power Management TLV: Specifically add or ensure the power management TLV is part of the configuration. This will advertise the PoE capabilities and requirements, enabling dynamic power allocation between the FortiSwitch and the connected devices (like VoIP phones or wireless access points). This can typically be done within the network-policy settings:
config med-network-policy
edit
set poe-capability
next
end
Save and Apply Changes: Exit the configuration blocks properly ensuring changes are saved:
End
Verify Configuration: It's always good practice to verify that your configurations have been applied correctly. Use the appropriate show or get commands to review the LLDP profile settings.
By adding the power management as part of LLDP-MED TLVs, the FortiSwitch will be able to communicate its power requirements and capabilities to the endpoints, thereby facilitating a dynamic power negotiation that is crucial for efficient PoE utilization.
Which LLDP-MED Type-Length-Values does FortiSwitch collect from endpoints to track network devices and determine their characteristics?
While FortiSwitch can collect all the listed LLDP-MED TLVs (Network Policy, Power Management, Location, and Inventory Management), the primary focus for tracking and identifying network devices is on the Inventory Management TLV.
This TLV carries critical details such as:
Manufacturer
Model
Hardware/Firmware versions
Serial/Asset numbers
This information provides a granular understanding of the devices on your network.