At ValidExamDumps, we consistently monitor updates to the Cisco 350-901 exam questions by Cisco. Whenever our team identifies changes in the exam questions,exam objectives, exam focus areas or in exam requirements, We immediately update our exam questions for both PDF and online practice exams. This commitment ensures our customers always have access to the most current and accurate questions. By preparing with these actual questions, our customers can successfully pass the Cisco Developing Applications using Cisco Core Platforms and APIs exam on their first attempt without needing additional materials or study guides.
Other certification materials providers often include outdated or removed questions by Cisco in their Cisco 350-901 exam. These outdated questions lead to customers failing their Cisco Developing Applications using Cisco Core Platforms and APIs exam. In contrast, we ensure our questions bank includes only precise and up-to-date questions, guaranteeing their presence in your actual exam. Our main priority is your success in the Cisco 350-901 exam, not profiting from selling obsolete exam questions in PDF or Online Practice Test.
Which two strategies are used to protect personally identifiable information? (Choose two.)
Explanation
Refer to the exhibit.
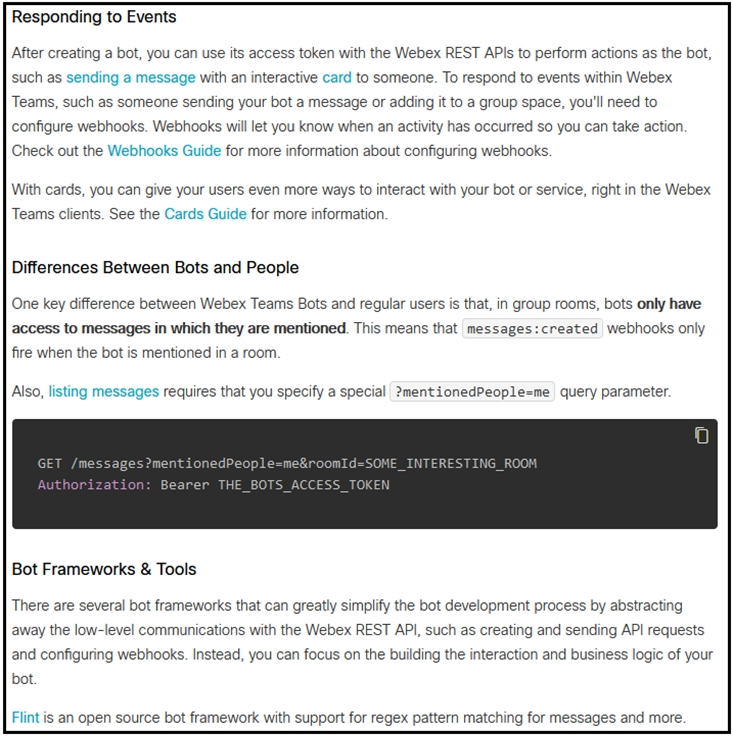
Which set of API requests must be executed by a Webex Teams bot after receiving a webhook callback to process messages in a room and reply with a new message back to the same room?
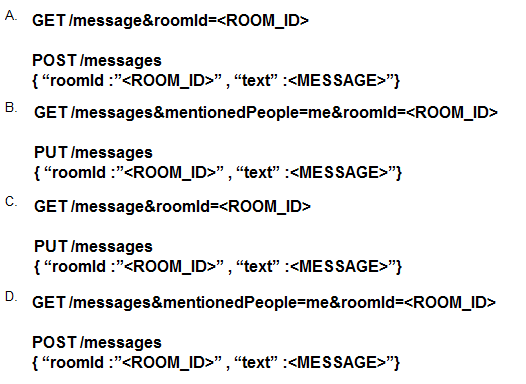
Refer to the exhibit.
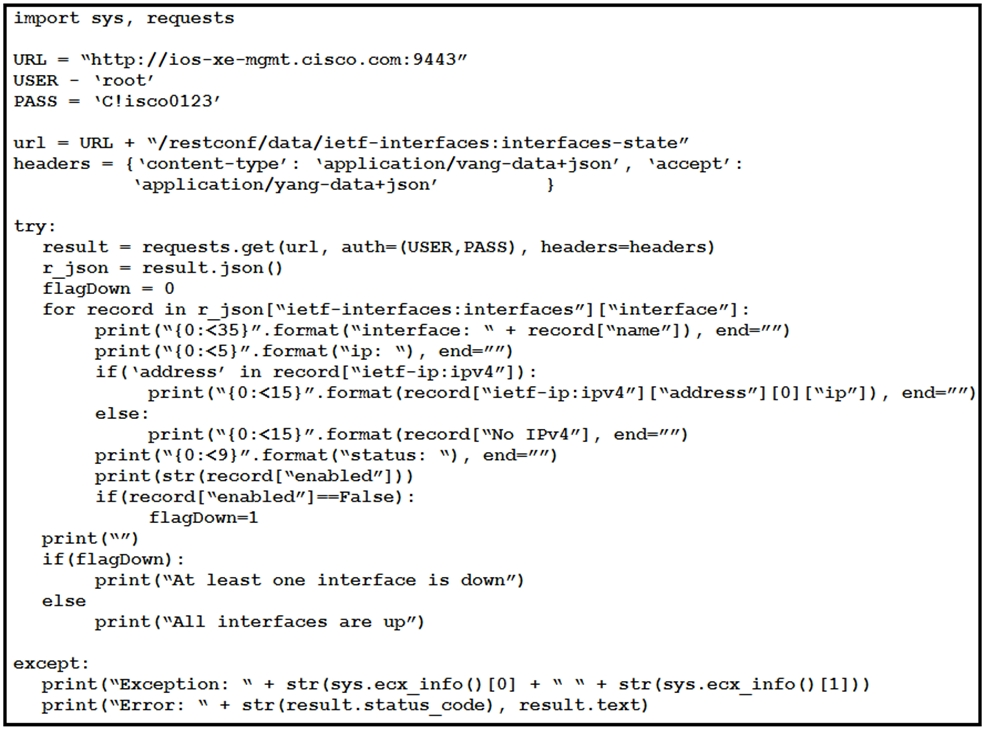
What is the output of this IOS-XE configuration program?
Refer to the exhibit.
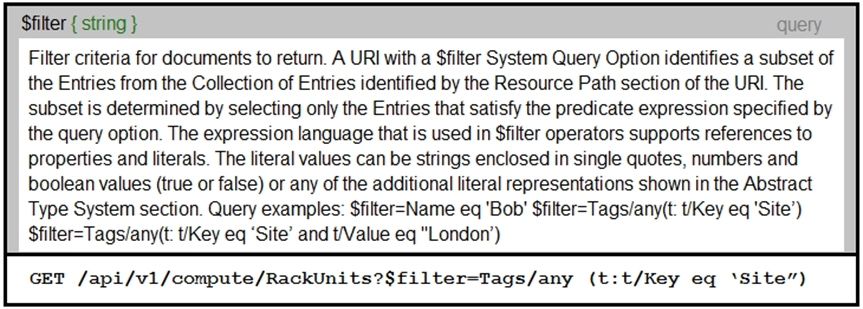
An Intersight API is being used to query RackUnit resources that have a tag keyword set to ''Site''. What is the expected output of this command?