At ValidExamDumps, we consistently monitor updates to the Cisco 350-201 exam questions by Cisco. Whenever our team identifies changes in the exam questions,exam objectives, exam focus areas or in exam requirements, We immediately update our exam questions for both PDF and online practice exams. This commitment ensures our customers always have access to the most current and accurate questions. By preparing with these actual questions, our customers can successfully pass the Cisco Performing CyberOps Using Core Security Technologies exam on their first attempt without needing additional materials or study guides.
Other certification materials providers often include outdated or removed questions by Cisco in their Cisco 350-201 exam. These outdated questions lead to customers failing their Cisco Performing CyberOps Using Core Security Technologies exam. In contrast, we ensure our questions bank includes only precise and up-to-date questions, guaranteeing their presence in your actual exam. Our main priority is your success in the Cisco 350-201 exam, not profiting from selling obsolete exam questions in PDF or Online Practice Test.
Refer to the exhibit.
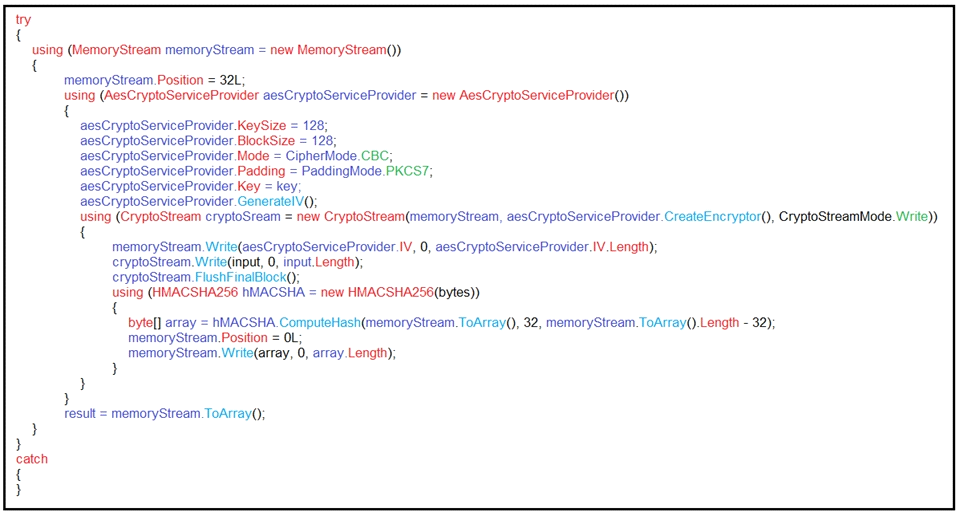
An engineer is performing a static analysis on a malware and knows that it is capturing keys and webcam events on a company server. What is the indicator of compromise?
Refer to the exhibit.
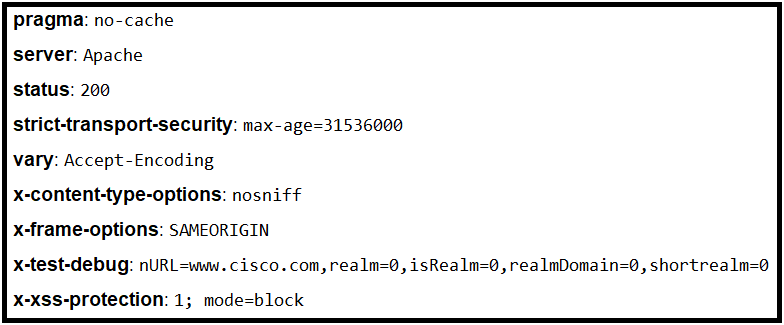
Where is the MIME type that should be followed indicated?
An engineer wants to review the packet overviews of SNORT alerts. When printing the SNORT alerts, all the packet headers are included, and the file is too large to utilize. Which action is needed to correct this problem?
%2F20201231%2Fus-east-1%2Fs3%2Faws4_request&X-Amz-Date=20201231T141156Z&X-Amz- Expires=172800&X-Amz-SignedHeaders=host&X-Amz- Signature=e122ab6eb1659e13b3bc6bb2451ce693c0298b76c1962c3743924bc5fd83d382
Which action should be taken when the HTTP response code 301 is received from a web application?