At ValidExamDumps, we consistently monitor updates to the Cisco 300-630 exam questions by Cisco. Whenever our team identifies changes in the exam questions,exam objectives, exam focus areas or in exam requirements, We immediately update our exam questions for both PDF and online practice exams. This commitment ensures our customers always have access to the most current and accurate questions. By preparing with these actual questions, our customers can successfully pass the Cisco Implementing Cisco Application Centric Infrastructure - Advanced exam on their first attempt without needing additional materials or study guides.
Other certification materials providers often include outdated or removed questions by Cisco in their Cisco 300-630 exam. These outdated questions lead to customers failing their Cisco Implementing Cisco Application Centric Infrastructure - Advanced exam. In contrast, we ensure our questions bank includes only precise and up-to-date questions, guaranteeing their presence in your actual exam. Our main priority is your success in the Cisco 300-630 exam, not profiting from selling obsolete exam questions in PDF or Online Practice Test.
What is the purpose of enabling ARP flooding when VMs are migrated from a pre-existing network to Cisco ACI and their gateways remain configured in the legacy setup?
Enabling ARP flooding is necessary when VMs are migrated from a pre-existing network to Cisco ACI and their gateways remain in the legacy setup. This allows the ACI fabric to learn about silent hosts that do not initiate communication, ensuring that the migrated VMs can communicate with all hosts in the network, including those that are silent.
How is the traffic directed to the firewall pair in a two-site Multi-Pod deployment with an active/standby firewall pair stretched across pods?
In a two-site Multi-Pod deployment with an active/standby firewall pair stretched across pods, traffic is directed to the pod with the active service node. This approach ensures that all traffic goes through the firewall that is currently handling traffic, maintaining security policies consistently across both sites while also providing high availability by automatically failing over to the standby firewall in case of any issues with the active one.Reference:= ( Implementing Cisco Application Centric Infrastructure Official Cert Guide )
Refer to the exhibit.
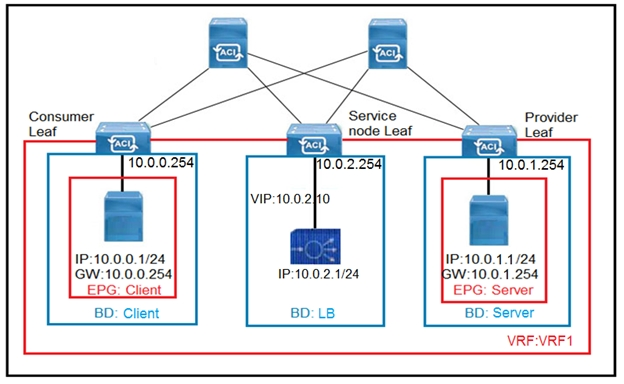
The client endpoint uses the load-balancer VIP as the destination address to send traffic to the server endpoint. If the load balancer does not do source NAT, which set of configurations must be applied on Cisco ACI to allow only the return traffic to be redirected to the service node?
To allow only the return traffic to be redirected to the service node when the load balancer does not perform source NAT, we need to configure aPolicy-Based Redirect (PBR). Here's how it can be achieved:
Create a Contract:
Create a contract linked to the common/default filter. This contract will define the communication rules between the client endpoint and the server endpoint.
Configure L4-L7 Device:
Create an L4-L7 device with the function type set to ''GoThrough.'' This device will be used to redirect traffic to the service node.
Create a Policy-Based Redirect Policy:
Set up a Policy-Based Redirect (PBR) policy.
Specify the L3 Destination as the load balancer's inside IP/MAC address.
Ensure that the L4-L7 Policy-Based Redirect Policy has the ''GoThrough'' function type.
Create a Service Graph Template:
Define a service graph template that references the previously created contract and L4-L7 device.
Apply the service graph template to the relevant connectors.
Connector Configuration:
On the consumer connector, reference the L4-L7 Policy-Based Redirect Policy.
On the provider connector, also reference the L4-L7 Policy-Based Redirect Policy.
By following this configuration, only the return traffic (from the server to the client) will be redirected to the service node, ensuring proper load balancing and traffic management.
Implementing Cisco Application Centric Infrastructure Official Cert Guide
Cisco ACI fabric is migrated from network-centric mode to application-centric mode. What is possible in an application-centric design?
In an application-centric design, the creation of additional EPGs under one bridge domain is possible. This allows for greater flexibility in managing and segmenting network traffic for different applications or services within the same bridge domain.
Refer to the exhibit.
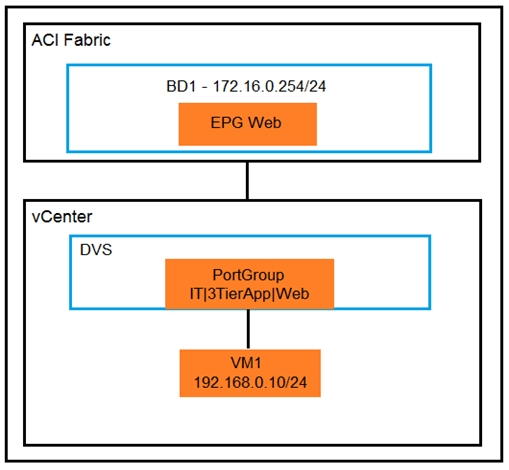
An organization migrates its virtualized servers from a legacy environment to Cisco ACI. VM1 is incorrectly attached to PortGroup IT|3TierApp|Web. Which action limits IP address learning in BD1?
To limit IP address learning in BD1 when VM1 is incorrectly attached to a PortGroup, enabling the Enforce Subnet Check is the correct action. This feature ensures that only IP addresses belonging to the defined subnets under the bridge domain are learned, preventing incorrect IP data from being disseminated across the network.Reference:= ( Implementing Cisco Application Centric Infrastructure Official Cert Guide )