At ValidExamDumps, we consistently monitor updates to the Cisco 300-440 exam questions by Cisco. Whenever our team identifies changes in the exam questions,exam objectives, exam focus areas or in exam requirements, We immediately update our exam questions for both PDF and online practice exams. This commitment ensures our customers always have access to the most current and accurate questions. By preparing with these actual questions, our customers can successfully pass the Cisco Designing and Implementing Cloud Connectivity exam on their first attempt without needing additional materials or study guides.
Other certification materials providers often include outdated or removed questions by Cisco in their Cisco 300-440 exam. These outdated questions lead to customers failing their Cisco Designing and Implementing Cloud Connectivity exam. In contrast, we ensure our questions bank includes only precise and up-to-date questions, guaranteeing their presence in your actual exam. Our main priority is your success in the Cisco 300-440 exam, not profiting from selling obsolete exam questions in PDF or Online Practice Test.
Refer to the exhibits.
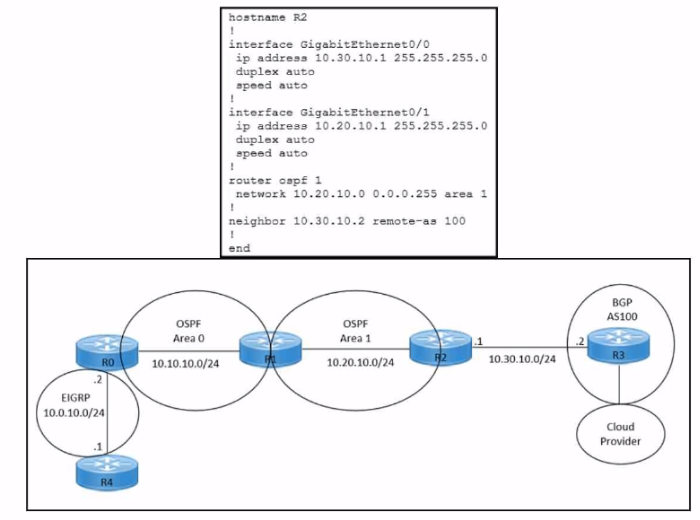
Refer to the exhibits. An engineer must redistribute OSPF internal routes into BGP to connect an on-premises network to a cloud provider without introducing extra routes. Which two commands must be configured on router R2? (Choose two.)
A company has multiple branch offices across different geographic locations and a centralized data center. The company plans to migrate Its critical business applications to the public cloud infrastructure that is hosted in Microsoft Azure. The company requires high availability, redundancy, and low latency for its business applications. Which connectivity model meets these requirements?
The connectivity model that meets the requirements of high availability, redundancy, and low latency for the company's business applications isExpressRoute with private peering using SDCI.
By using ExpressRoute with private peering and SDCI, the company can achieve the following benefits:
Refer to the exhibits.
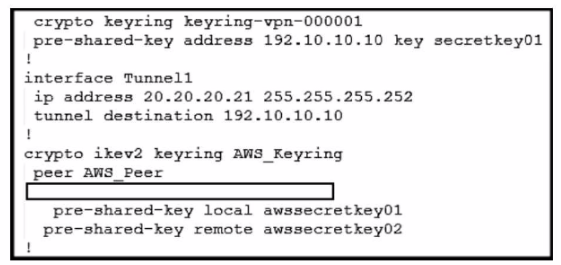
Refer to the exhibit. An engineer needs to configure a site-to-site IPsec VPN connection between an on-premises Cisco IOS XE router and Amazon Web Services (AWS). Which configuration command must be placed in the blank in the code to complete the tunnel configuration?
Configure IOS-XE Site-to-Site VPN Connection to Amazon Web Services - Cisco Community
[Security for VPNs with IPsec Configuration Guide, Cisco IOS XE Release 3S - Config
Refer to the exhibit.
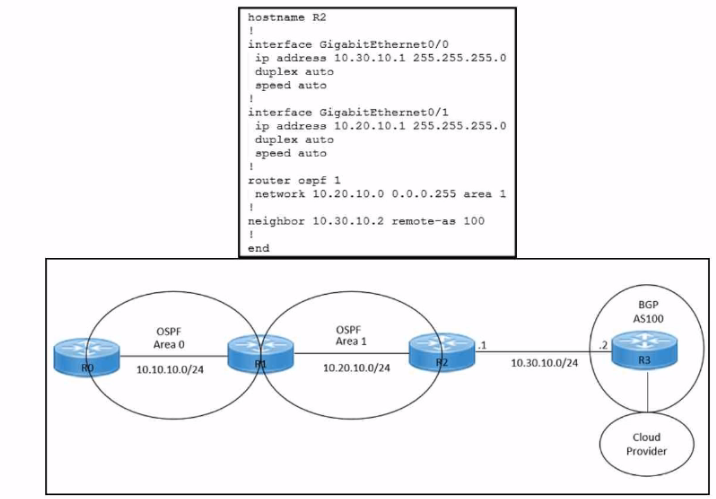
Refer to the exhibits. An engineer must redistribute IBGP routes into OSPF to connect an on-premises network to a cloud provider. Which command must be configured on router R2?
I hope this helps you understand the question and the answer. If you have any other questions or requests, please let me know. I am always happy to help.
Refer to the exhibits.
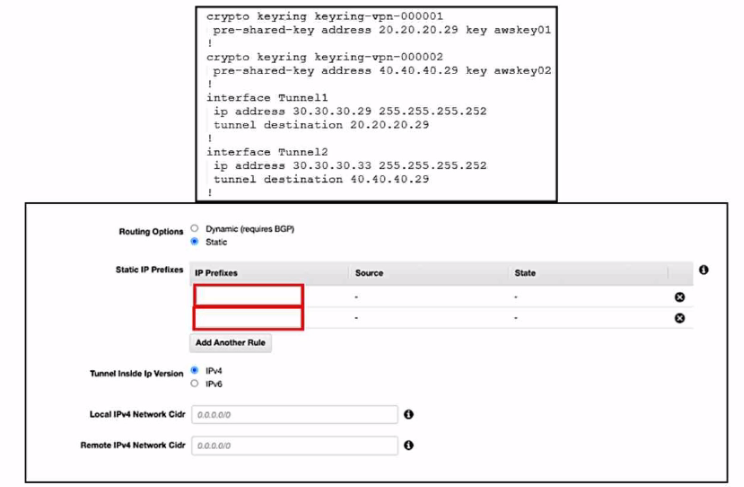
Refer to the exhibits. An engineer needs to configure a site-to-site IPsec VPN connection between an on premises Cisco IOS XE router and Amazon Web Services (AWS). Which two IP prefixes should be used to configure the AWS routing options? (Choose two.)