At ValidExamDumps, we consistently monitor updates to the Cisco 300-215 exam questions by Cisco. Whenever our team identifies changes in the exam questions,exam objectives, exam focus areas or in exam requirements, We immediately update our exam questions for both PDF and online practice exams. This commitment ensures our customers always have access to the most current and accurate questions. By preparing with these actual questions, our customers can successfully pass the Cisco Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies exam on their first attempt without needing additional materials or study guides.
Other certification materials providers often include outdated or removed questions by Cisco in their Cisco 300-215 exam. These outdated questions lead to customers failing their Cisco Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies exam. In contrast, we ensure our questions bank includes only precise and up-to-date questions, guaranteeing their presence in your actual exam. Our main priority is your success in the Cisco 300-215 exam, not profiting from selling obsolete exam questions in PDF or Online Practice Test.
An attacker embedded a macro within a word processing file opened by a user in an organization's legal department. The attacker used this technique to gain access to confidential financial dat
a. Which two recommendations should a security expert make to mitigate this type of attack? (Choose two.)
A scanner detected a malware-infected file on an endpoint that is attempting to beacon to an external site. An analyst has reviewed the IPS and SIEM logs but is unable to identify the file's behavior. Which logs should be reviewed next to evaluate this file further?
Refer to the exhibit.
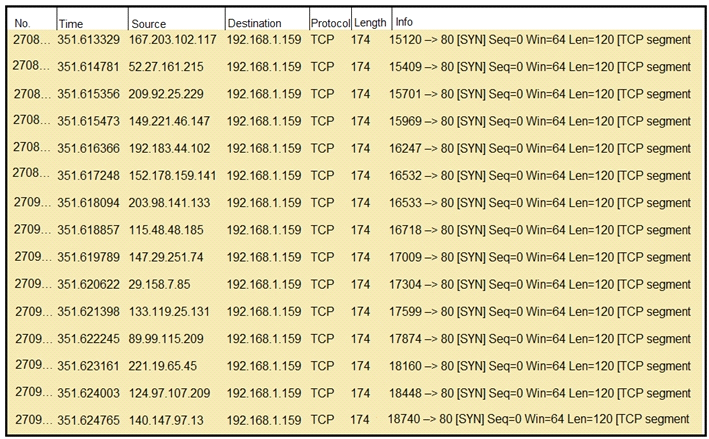
What should an engineer determine from this Wireshark capture of suspicious network traffic?