At ValidExamDumps, we consistently monitor updates to the Arcitura Education S90.20 exam questions by Arcitura Education. Whenever our team identifies changes in the exam questions,exam objectives, exam focus areas or in exam requirements, We immediately update our exam questions for both PDF and online practice exams. This commitment ensures our customers always have access to the most current and accurate questions. By preparing with these actual questions, our customers can successfully pass the Arcitura Education SOA Security Lab exam on their first attempt without needing additional materials or study guides.
Other certification materials providers often include outdated or removed questions by Arcitura Education in their Arcitura Education S90.20 exam. These outdated questions lead to customers failing their Arcitura Education SOA Security Lab exam. In contrast, we ensure our questions bank includes only precise and up-to-date questions, guaranteeing their presence in your actual exam. Our main priority is your success in the Arcitura Education S90.20 exam, not profiting from selling obsolete exam questions in PDF or Online Practice Test.
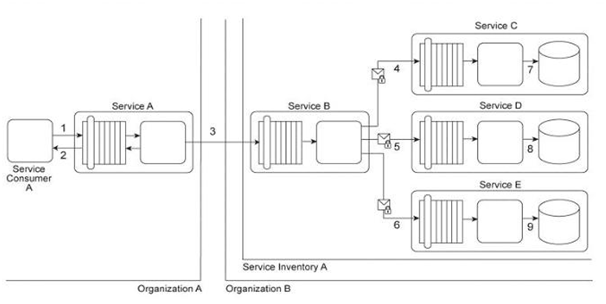
Service Consumer A sends a request to Service A (1). Service A replies with an acknowledgement message (2) and then processes the request and sends a request message to Service B (3). This message contains confidential financial data. Service B sends three different request messages together with its security credentials to Services C, D, and E (4, 5, 6). Upon successful authentication, Services C, D, and E store the data from the message in separate databases (7, 8, 9) Services B, C, D, and E belong to Service Inventory A, which further belongs to Organization B .Service Consumer A and Service A belong to Organization A .The service contracts of Services A and B both comply with the same XML schema. However, each organization employs different security technologies for their service architectures. To protect the confidential financial data sent by Service A to Service B, each organization decides to independently apply the Data Confidentiality and the Data Origin Authentication patterns to establish message-layer security for external message exchanges. However, when an encrypted and digitally signed test message is sent by Service A to Service B, Service B was unable to decrypt the message. Which of the following statements describes a solution that solves this problem?
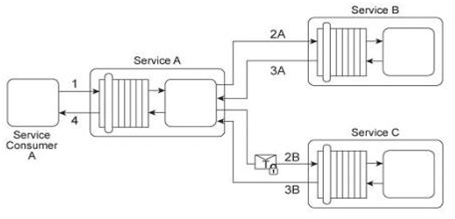
Service A is a publically accessible service that provides free multimedia retrieval capabilities to a range of service consumers. To carry out this functionality, Service A is first invoked by Service Consumer A (1). Based on the nature of the request message received from Service Consumer A, Service A either invokes Service B or Service C .When Service B is invoked by Service A (2A) it retrieves data from publicly available sources (not shown) and responds with the requested data (3A). When Service C is invoked by Service A (2B) it retrieves data from proprietary sources within the IT enterprise (not shown) and responds with the requested data (3B). After receiving a response from Service B or Service C, Service A sends the retrieved data to Service Consumer A (4). Service B does not require service consumers to be authenticated, but Service C does require authentication of service consumers. The service contract for Service A therefore uses WS-Policy alternative policies in order to express the two different authentication requirements to Service Consumer A .When Service Consumer A sends a request message (1), Service A determines whether the request requires the involvement of Service C and then checks to ensure that the necessary security credentials were received as part of the message. If the credentials provided by Service Consumer A are verified. Service A creates a signed SAML assertion and sends it with the request message to Service C (2B) This authentication information is protected by public key encryption However, responses to Service Consumer A's request message (3B, 4) are not encrypted for performance reasons. Recently, the usage of Service C has noticeably declined. An investigation has revealed response messages issued by Service C (3B) have been repeatedly intercepted and accessed by unauthorized and malicious intermediaries. As a result, Service Consumer A has lost confidence in the use of Service A for the retrieval of proprietary data because it is being viewed as a security risk. This is especially troubling, because the owner of Service A had planned to start charging a fee for Service A's ability to provide proprietary data via the use of Service C .How can this service composition architecture be changed to address the security problem with minimal impact on runtime performance?
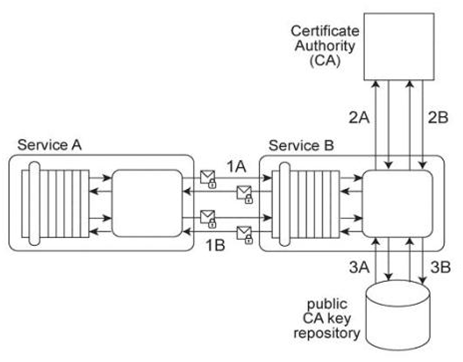
Service A exchanges messages with Service B multiple times during the same runtime service activity. Communication between Services A and B has been secured using transport-layer security. With each service request message sent to Service B (1A .IB), Service A includes an X.509 certificate, signed by an external Certificate Authority (CA). Service B validates the certificate by retrieving the public key of the CA (2A .2B) and verifying the digital signature of the X.509 certificate. Service B then performs a certificate revocation check against a separate external CA repository (3A, 3B). No intermediary service agents reside between Service A and Service B .Service B has recently suffered from poor runtime performance plus it has been the victim of an access-oriented attack. As a result, its security architecture must be changed to fulfill the following new requirements:
1. The performance of security-related processing carried out by Service B when communicating with Service A must be improved.
2. All request messages sent from Service A to Service B must be screened to ensure that they do not contain malicious content. Which of the following statements describes a solution that fulfills these requirements?
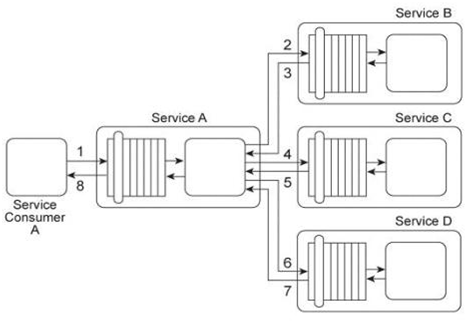
Service A provides a data retrieval capability that can be used by a range of service consumers, including Service Consumer A, In order to retrieve the necessary data. Service Consumer A first sends a request message to Service A (1). Service A then exchanges request and response messages with Service B (2, 3). Service C (4, 5), and Service D (6. 7). After receiving all three response messages from Services B .C .and D, Service A assembles the collected data into a response message that it returns to Service Consumer A (8). The Service A data retrieval capability has been suffering from poor performance, which has reduced its usefulness to Service Consumer A .Upon studying the service composition architecture, it is determined that the performance problem can be partially attributed to redundant validation by service contracts for compliance to security policies. Services B and C have service contracts that contain the same two security policies. And, Service D has a service contract that contains a security policy that is also part of Service A's service contract. What changes can be made to the service contracts in order to improve the performance of the service composition while preserving the security policy compliance requirements?
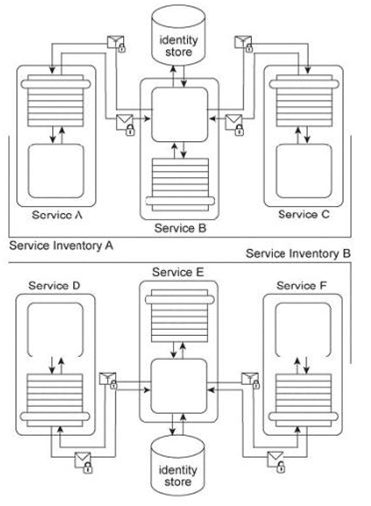
Services A, B, and C reside in Service Inventory A and Services D, E, and F reside in Service Inventory B .Service B is an authentication broker that issues WS-Trust based SAML tokens to Services A and C upon receiving security credentials from Services A and C .Service E is an authentication broker that issues WS-Trust based SAML tokens to Services D and F upon receiving security credentials from Services D and E .Service B uses the Service Inventory A identify store to validate the security credentials of Services A and C .Service E uses the Service Inventory B identity store to validate the security credentials of Services D and F .To date, the two service inventories have existed independently from each other. However, a requirement has emerged that the services in Service Inventory A need to be able to use the services in Service Inventory B, and vice versa. How can cross-service inventory message exchanges be enabled with minimal changes to the existing service inventory architectures and without introducing new security mechanisms?