At ValidExamDumps, we consistently monitor updates to the Arcitura Education S90.08B exam questions by Arcitura Education. Whenever our team identifies changes in the exam questions,exam objectives, exam focus areas or in exam requirements, We immediately update our exam questions for both PDF and online practice exams. This commitment ensures our customers always have access to the most current and accurate questions. By preparing with these actual questions, our customers can successfully pass the Arcitura Education SOA Design & Architecture Lab with Services & Microservices exam on their first attempt without needing additional materials or study guides.
Other certification materials providers often include outdated or removed questions by Arcitura Education in their Arcitura Education S90.08B exam. These outdated questions lead to customers failing their Arcitura Education SOA Design & Architecture Lab with Services & Microservices exam. In contrast, we ensure our questions bank includes only precise and up-to-date questions, guaranteeing their presence in your actual exam. Our main priority is your success in the Arcitura Education S90.08B exam, not profiting from selling obsolete exam questions in PDF or Online Practice Test.
Refer to Exhibit.
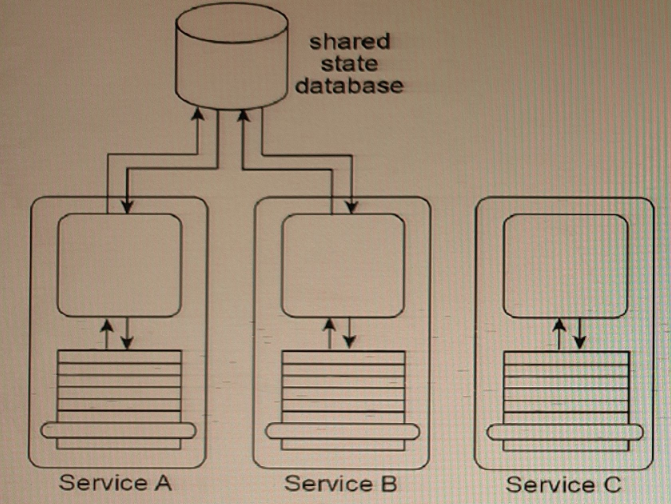
Services A, B, and C are non-agnostic task services. Service A and Service B use the same shared state database to defer their state data at runtime.
An assessment of the three services reveals that each contains some agnostic logic that cannot be made available for reuse because it is bundled together with non-agnostic logic.
The assessment also determines that because Service A, Service B and the shared state database are each located in physically separate environments, the remote communication required for Service A and Service B to interact with the shared state database is causing an unreasonable decrease in runtime performance.
How can the application of the Orchestration pattern improve this architecture?
The application of the Orchestration pattern can improve this architecture by cleanly separating the non-agnostic logic from the agnostic logic, allowing the design of new agnostic services with reuse potential. The State Repository pattern, which is supported by and local to the orchestration environment, provides a central state database that can be shared by Services A and B. The local state database avoids problems with remote communication. Additionally, the Orchestration pattern provides a central controller that can coordinate the interactions between Services A, B, and C, reducing the need for remote communication between services and improving runtime performance.
Refer to Exhibit.
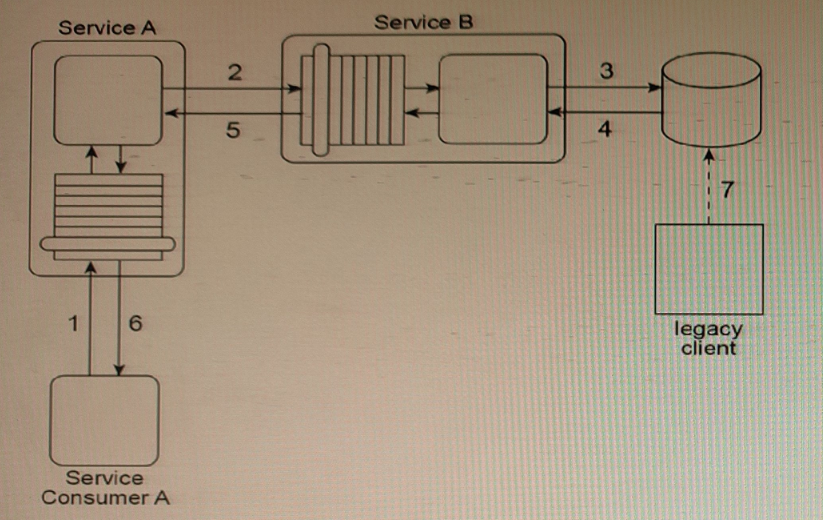
Service A is an entity service that provides a Get capability which returns a data value that is frequently changed.
Service Consumer A invokes Service A in order to request this data value (1). For Service A to carry out this request, it must invoke Service B (2), a utility service that interacts (3, 4) with the database in which the data value is stored. Regardless of whether the data value changed, Service B returns the latest value to Service A (5), and Service A returns the latest value to Service Consumer A (6).
The data value is changed when the legacy client program updates the database (7). When this change will occur is not predictable. Note also that Service A and Service B are not always available at the same time.
Any time the data value changes, Service Consumer A needs to receive It as soon as possible. Therefore, Service Consumer A initiates the message exchange shown In the figure several times a day. When it receives the same data value as before, the response from Service A Is ignored. When Service A provides an updated data value, Service Consumer A can process it to carry out its task.
The current service composition architecture is using up too many resources due to the repeated invocation of Service A by Service Consumer A and the resulting message exchanges that occur with each invocation.
What steps can be taken to solve this problem?
This solution is the most appropriate one among the options presented. By using the Event-Driven Messaging pattern, Service A can be notified of changes to the data value without having to be invoked repeatedly by Service Consumer A, which reduces the resources required for message exchange. Asynchronous Queuing ensures that the event notification message is not lost due to the unavailability of Service A or Service B. This approach improves the efficiency of the service composition architecture.
Refer to Exhibit.
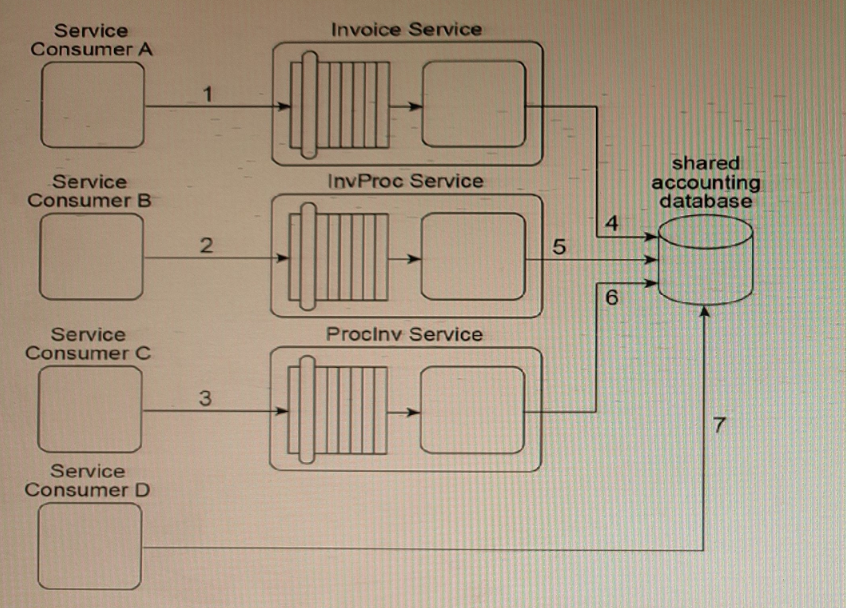
Our service inventory contains the following three services that provide Invoice-related data access capabilities: Invoice, InvProc and Proclnv. These services were created at different times by different project teams and were not required to comply with any design standards. Therefore, each of these services has a different data model for representing invoice data.
Currently, each of these three services has a different service consumer: Service Consumer A accesses the Invoice service (1), Service Consumer B (2) accesses the InvProc service, and Service Consumer C (3) accesses the Proclnv service. Each service consumer invokes a data access capability of an invoice-related service, requiring that service to interact with the shared accounting database that is used by all invoice-related services (4, 5, 6).
Additionally, Service Consumer D was designed to access invoice data from the shared accounting database directly (7). (Within the context of this architecture, Service Consumer D is labeled as a service consumer because it is accessing a resource that is related to the illustrated service architectures.)
Assuming that the Invoice service, InvProc service and Proclnv service are part of the same service inventory, what steps would be required to fully apply the Official Endpoint pattern?
he Legacy Wrapper pattern can be applied so that Component B is separated into a separate utility service that wraps the shared database. The Legacy Wrapper pattern can be applied again so that Component C is separated into a separate utility service that acts as a wrapper for the legacy system API. The Legacy Wrapper pattern can be applied once more to Component D so that it is separated into another utility service that provides standardized access to the file folder. The Service Facade pattern can be applied so that three facade components are added: one between Component A and each of the new wrapper utility services. This way, the facade components can compensate for any change in behavior that may occur as a result of the separation. The Service Composability principle can be further applied to Service A and the three new wrapper utility services so that all four services are optimized for participation in the new service composition. This will help make up for any performance loss that may result from splitting the three components into separate services.
By applying the Legacy Wrapper pattern to separate Components B, C, and D into three different utility services, the shared resources within the IT enterprise (Database A, the legacy system, and the file folders) can be properly encapsulated and managed by dedicated services. The Service Facade pattern can then be used to create a facade component between Component A and each of the new wrapper utility services, allowing them to interact seamlessly without affecting Service Consumer A's behavior.
Finally, the Service Composability principle can be applied to ensure that Service A and the three new wrapper utility services are optimized for participation in the new service composition. This will help to mitigate any performance loss that may result from splitting the three components into separate services.
Refer to Exhibit.

Service Consumer A and Service A reside in Service Inventory
The Asynchronous Queuing pattern is applied to position a messaging queue between Service A, Service B, Service C, Service D, and Service Consumer A. This ensures that messages can be passed between these services without having to be in a stateful mode.
The Data Model Transformation and Protocol Bridging patterns are applied to enable communication between Service A and Service B, Service A and Service C, and Service A and Service D, despite their different data models and transport protocols.
The Redundant Implementation pattern is applied to bring a copy of Service D in-house to ensure that it can be accessed locally and reduce the unpredictability of its performance.
The Legacy Wrapper pattern is applied to wrap Service D with a standardized service contract that complies with the design standards used in Service Inventory B. This is useful for service consumers who want to use Service D but do not want to change their existing applications or service contracts.
Overall, this approach provides a comprehensive solution that addresses the issues with Service A, Service B, Service C, and Service D, while maintaining compliance with the Service Abstraction principle.
Refer to Exhibit.

Service A is a task service that is required to carry out a series of updates to a set of databases in order to complete a task. To perform the database updates. Service A must interact with three other services that each provides standardized data access capabilities.
Service A sends its first update request message to Service B (1), which then responds with a message containing either a success or failure code (2). Service A then sends its second update request message to Service C (3), which also responds with a message containing either a success or failure code (4). Finally, Service A sends a request message to Service D (5), which responds with its own message containing either a success or failure code (6).
Services B, C and D are agnostic services that are reused and shared by multiple service consumers. This has caused unacceptable performance degradation for the service consumers of Service A as it is taking too long to complete its overall task. You've been asked to enhance the service composition architecture so that Service A provides consistent and predictable runtime performance. You are furthermore notified that a new type of data will be introduced to all three databases. It is important that this data is exchanged in a standardized manner so that the data model used for the data in inter-service messages is the same.
What steps can be taken to fulfill these requirements?
This approach isolates the services used by Service A, allowing it to avoid the performance degradation caused by multiple service consumers. By creating redundant implementations of Services B, C, and D that are accessed only by Service A, the Composition Autonomy pattern also ensures that Service A's runtime performance is consistent and predictable. Applying the Canonical Schema pattern ensures that the new type of data is exchanged in a standardized manner, ensuring consistent representation of the data model used for the data in inter-service messages.