At ValidExamDumps, we consistently monitor updates to the Arcitura Education C90.03 exam questions by Arcitura Education. Whenever our team identifies changes in the exam questions,exam objectives, exam focus areas or in exam requirements, We immediately update our exam questions for both PDF and online practice exams. This commitment ensures our customers always have access to the most current and accurate questions. By preparing with these actual questions, our customers can successfully pass the Arcitura Education Cloud Technology Lab exam on their first attempt without needing additional materials or study guides.
Other certification materials providers often include outdated or removed questions by Arcitura Education in their Arcitura Education C90.03 exam. These outdated questions lead to customers failing their Arcitura Education Cloud Technology Lab exam. In contrast, we ensure our questions bank includes only precise and up-to-date questions, guaranteeing their presence in your actual exam. Our main priority is your success in the Arcitura Education C90.03 exam, not profiting from selling obsolete exam questions in PDF or Online Practice Test.
Cloud Service Consumer A invokes Cloud Service A from Cloud X (owned by Cloud Provider X) (1). To fulfill the request from Cloud Service Consumer A, Cloud Service A needs to invoke Cloud Service B that resides on Cloud Y (owned by Cloud Provider Y) (2). After completing its processing, Cloud Service B sends a response to Cloud Service A (3). Cloud Service A verifies the response and then finally sends its response to Cloud Service Consumer A (4).
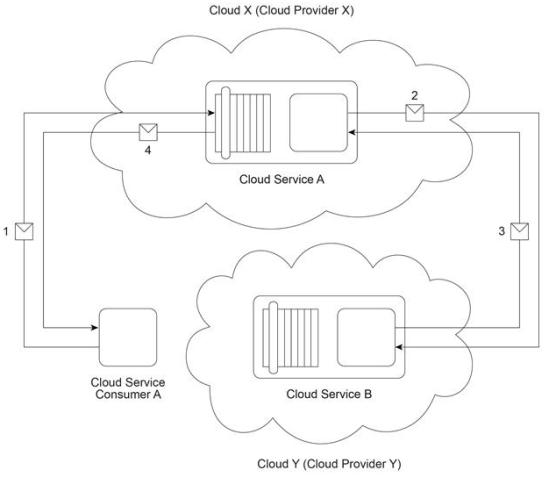
The guaranteed availability of the Cloud Service A implementation is 95% and the guaranteed availability of the Cloud Service B implementation is 95%. Which of the following statements accurately describes the actual availability that Cloud Service Consumer A can receive based on the described scenario?
Cloud Consumer A (the organization that owns Cloud Service Consumer A) needs regular access to an external, cloud-based Weather Service that provides up-to-date weather forecast information. Cloud Providers X, Y and Z are competing public cloud providers, each offering a Weather Service with the features required by Cloud Consumer A .

Based on the provided statistics, which cloud provider can offer a Weather Service with the least amount of projected downtime?
Cloud Service Consumer A accesses Cloud Service A (1) that resides in Cloud X. a private cloud owned by the same organization acting as Cloud Consumer A . Cloud Service A processes the message from Cloud Service Consumer A and then sends back a response with the requested data (2). Next, Cloud Service Consumer A sends a message containing some of this data to Cloud Service B (3), which resides in public Cloud Y that is owned by Cloud Provider Y. After processing the message, Cloud Service B sends back a response with additional data to Cloud Service Consumer A (4). Finally, Cloud Service Consumer A writes the data it collected from Cloud Services A and B to Database A (5).

Recently, Cloud Service Consumer A has been required to access Cloud Services A and B at a significantly higher rate, sometimes over 1,000 times within a given workday. This increased usage has not affected Cloud Service B's performance. Cloud Service A, however, has been generating runtime exceptions and responses to Cloud Service Consumer A have become increasingly slow and unreliable. It is determined that this decline in performance is due to infrastructure limitations within private Cloud X's environment. Instead of investing in new infrastructure for Cloud X, it is decided to explore the feasibility of moving Cloud Service A to Cloud Y instead. Which of the following statements describe valid financial considerations that can be taken into account for assessing the feasibility of this move?
Cloud Provider X (which owns Cloud X) deploys two physical servers (Physical Servers A and B) and two databases (Databases A and B). Virtual Servers A and B are hosted by Physical Server A and Ready-Made Environments A and B are hosted by Virtual Server B . Virtual Servers C and D are hosted by Physical Server B . Cloud Service Consumer A regularly accesses Virtual Server D in order to test and deploy a new cloud service that was developed on-premise by the cloud consumer organization operating Cloud Service Consumer A . Cloud Service Consumer B (operated by a different cloud consumer organization) has been regularly accessing Ready-Made Environment A in order to develop and deploy a different new cloud service.
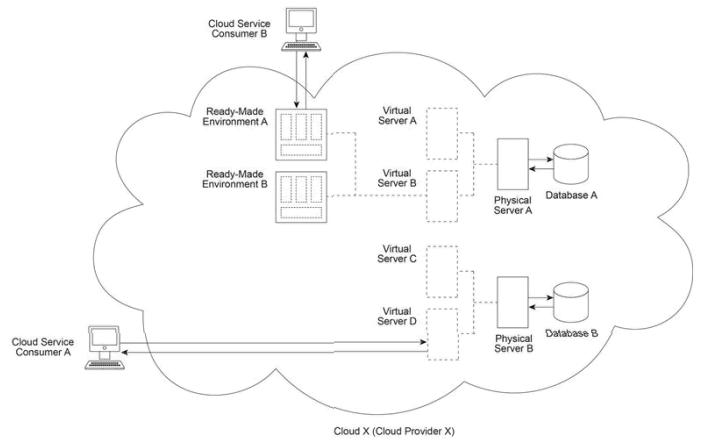
Cloud X is a private cloud that, to-date, has been set up within the cloud provider company to provision IT resources free of charge to internal cloud consumers, via PaaS and IaaS delivery models. The cloud consumers that have been operating Cloud Service Consumers A and B represent different IT departments within the company that have been working separately on the development of new cloud services. Cloud Service Consumer A has been accessing Virtual Server D to make necessary configurations and administration settings for the upcoming deployment of a new cloud service that was previously developed outside of Cloud X. Cloud Service Consumer B has been accessing Ready-Made Environment A to develop and now deploy a different new cloud service. Cloud Provider X (which is represented by a separate IT department dedicated to governing and administering Cloud X) determines that it will need to introduce three specific enhancements to Cloud X in order to accommodate both upcoming cloud services. First, it needs to add a way to charge cloud consumers for the usage of cloud services. Secondly, it needs to add a way for new cloud services to be automatically scaled. Finally, it needs to add a way for a cloud consumer to be automatically notified when a cloud service encounters runtime loads that exceed its allocated usage threshold. Which of the following statements accurately describes a solution that fulfills all three identified requirements?
Cloud Provider Y owns Cloud Y, which provides a set of cloud services, virtual servers and one physical server. Cloud Services A and B are hosted on Virtual Server A, which is hosted by Physical Server A . Physical Server A also hosts Virtual Server B, which hosts redundant implementations of Cloud Services A and B for load balancing purposes. Cloud Service Consumer A is accessing Cloud Service A located on Virtual Server A . Cloud Service Consumer B is accessing Cloud Service B located on Virtual Server B . Cloud Service Consumers A and B are both owned by Cloud Consumer X. Cloud Consumer X has recently complained that Cloud Services A and B have become less available than what is guaranteed in their service level agreements (SLAs). Cloud Provider Y launches an investigation that reveals that Virtual Servers A and B have been subjected to denial of service attacks. This is confirmed as the cause of the decline in the availability of Cloud Services A and B.
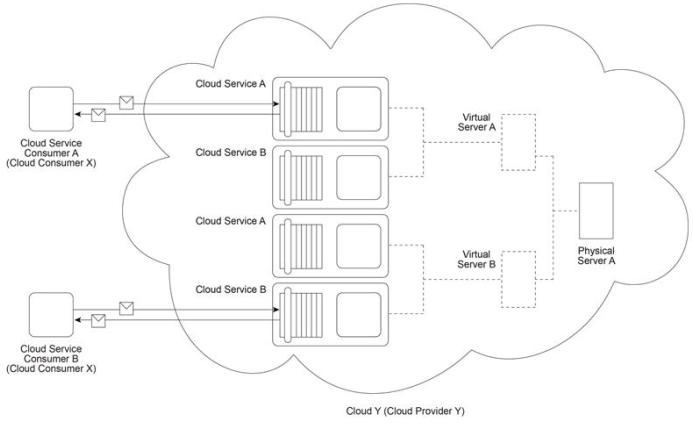
Which of the following statements describes a solution that can increase the availability of Cloud Services A and B?